 |
CLIQUENET FAQ |
- What is CliqueNet ?
-
It's a peer-to-peer, self-organizing system and associated
communication protocol for anonymous communication.
- What does CliqueNet do ?
-
CliqueNet anonymizes all communication on the network. Someone capable
of wiretapping anywhere and everywhere on the Internet cannot
definitively determine either the sender or the receiver of a packet.
- Why would anyone want to be anonymous ?
-
Strong anonymity and privacy guarantees are critical for many offline,
real-world applications. Whether casting a ballot in a voting booth,
engaging in a cash-based financial transaction, or getting tested for
certain medical conditions, people expect that the transaction by
itself will not reveal their identity. Such transactions require
strong anonymity, where a party to a transaction needs to
unconditionally hide their identity from other participants and
possible eavesdroppers. Many other applications require strong
privacy, where participants release their identity to other parties of
their choice, but need to cloak it from unauthorized interceptors. For
instance, whistleblowers, witnesses, patients, press sources,
attorneys and clients, among many others, call for protection from
third parties who might deduce their identity via traffic
analysis. Indeed, anonymity and privacy are deemed so indispensable
for a functional society that many countries have codified special
protections into law.
- How much privacy do I currently have on the Internet ?
-
None. Someone who is monitoring traffic in the core routers can
determine which sites you communicate with. Someone who is monitoring
users at your ISP can match your IP address to your physical
address. Relevant cartoon.
- What are the goals of CliqueNet ?
-
The overall goals of CliqueNet are:
- Strong Anonymity: The system should provide strong, that is,
computationally insurmountable, mechanisms to guard the identities
of participants. CliqueNet ensures that even an adversary with
access to every internal packet cannot determine the identities of
senders and receivers.
- High Scalability: The communication protocol should achieve
performance that does not degrade significantly as more
participants join the network. CliqueNet automatically divides the
network into smaller cells, or cliques, and uses ad hoc routing to
route for inter-clique communication.
- Robustness: Anonymous communication protocols need to be
especially robust against denial of service attacks and malicious
hosts, as the anonymous medium makes it easier for disruptive hosts
to launch Byzantine with impunity. CliqueNet provides irrefutable,
non-forgeable proofs to identify disruptive nodes and exclude them
from the network.
- What are the contributions of CliqueNet ?
-
This work makes three contributions. First, it proposes a novel scheme
for achieving strong anonymity and scalability in the same system by
combining DC-nets with ad hoc routing protocols. Second, it introduces
the concept of a disruption proof to allow legitimate clique members
to detect and exclude misbehaving hosts, without allowing malicious
hosts to forge such certificates. Finally, we have built the first
physical implementation of DC-nets, shown that it does
not scale, and extended it into CliqueNet, that is secure and scales
better.
- How does CliqueNet achieve anonymity ?
-
CliqueNet combines the strong anonymity and privacy properties of
DC-nets with a divide-and-conquer approach that enables the system to
scale well with increasing numbers of hosts. CliqueNet automatically
constructs small anonymizing cliques that use an extended version of
the basic, strong DC-net mechanism. CliqueNet provides an ad hoc
routing protocol for routing packets between cliques while preserving
the identity of the endpoints. The protocol also embodies
cryptographic commitments, join certificates, and disruption proofs to
identify and exclude misbehaving hosts.
- How does CliqueNet differ from Crowds, MIXNET, and Onion Routing ? How
is it different from the anonymization scheme used in Freenet and
Gnutella ?
-
CliqueNet differs from previous anonymous communication protocols in
several important ways. Previous implementations of anonymous
communication protocols and identity protection schemes have relied
principally on source rewriting [C81, RR98, RSG98, GW97, CSW+00, G01]
? in essence, every router in a chain replaces the source address in a
packet with its own, thereby obfuscating the originator?s
identity. While such schemes are simple and scalable, they cannot
provide strong anonymity guarantees. A powerful adversary that can
capture traffic within and around the anonymizing network can perform
statistical traffic analyses and corroborate the identity of users
with sent packets. Further, such schemes are fragile, as a node that
stops transmitting for any reason disrupts the communication path for
all traffic that was routed through it.
- How is CliqueNet similar to or different from DC-nets ?
-
CliqueNet is based on DC-nets, originally proposed by Chaum in 1988.
DC-nets are a heavy-weight alternative for anonymous communication that
addresses the traffic analysis problem. DC-nets provide an
information-theoretic guarantee that even an observer that captures
every packet cannot determine the originator. However, traditional
DC-nets do not scale: the aggregate bandwidth of a DC-net follows
O(1/N^2). Consequently, no practical implementation of DC-nets has been
reported in the literature to date. Our implementation is the first reported
instance of DC-net deployment. Our bandwidth measurements, collected
in a switched ethernet cluster of 18 nodes, documents that the
bandwidth falls off with the square of the number of hosts.
- How do DC nets work ?
-
CliqueNet is based on Dining-Cryptographer networks, or DC-nets,
originally suggested by Chaum in [C88]. DC-nets propagate a bit of
information in the following way: suppose we have two participants,
Alice and Bob, one of whom (e.g. Bob) would like to communicate a
one-bit message to Charlie, but Alice and Bob want to hide the
identity of the message originator. They first toss a coin in
secret. Alice sends the truthful result of the coin flip to
Charlie. Bob, on the other hand, reports the true result of the coin
toss only if he wants to transmit a 0. If he wants to transmit a 1,
Bob lies about the coin flip. Charlie deciphers the message by XOR?ing
the values sent by Alice and Bob. If they both call out heads or
tails, they are both telling the truth and the one-bit message is a
zero; otherwise, one of them is lying, and the one-bit message is a
one. Since Charlie does not know if it was Alice or Bob who lied about
the coin toss, he can never determine who sent the message. This
security guarantee is strong and information-theoretic: no amount of
computational power can help Charlie determine that it was Bob who
sent the message.
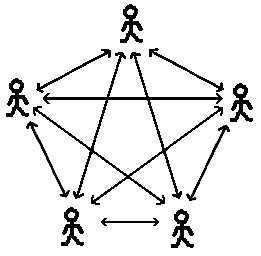
- Neat, but does that generalize to a full-blown system ?
-
Chaum showed that turning this basic idea into a general scheme for
communication between arbitrary numbers of hosts is
straightforward. Typically, all participants will require anonymity,
which can be achieved by arranging all the participants in a fully
connected graph. Every pair of nodes with an edge between them share a
virtual coin. The coin tosses are generated in blocks by a
pseudo-random number generator. Instead of wasting bandwidth to
exchange the pseudo-random stream, members use a standard secure key
exchange protocol to perform a pairwise exchange of initial seeds.
- How can I find out more about the technical details of CliqueNet ?
-
The papers on our papers page and the related work page can help


