

Cornell University
Computer Science Department
Masters of Engineering Project
Spring 1998
Han-Yang Lo
Sanjeev Topiwala
Joyce Wang
with
assistance from Keith Sollers
Under the supervision of:
Professor Fred B. Schneider
last
modified: Monday, 4/27/98
System Architecture
Component Architecture
Driver
Program
Network Services
File
Services
The v-óa$h system is composed of five main modules: file/data services, cryptographic services, network services, driver program, and user interface (as shown in the following illustration).

The driver program provides an extra layer of security by preventing direct access to the underlying subsystems. All interactions between the subsystems must pass through the driver. This provides for a smaller trusted computing base (TCB). The module categories were designed to isolate unrelated services, reducing the complexity of the overall system.
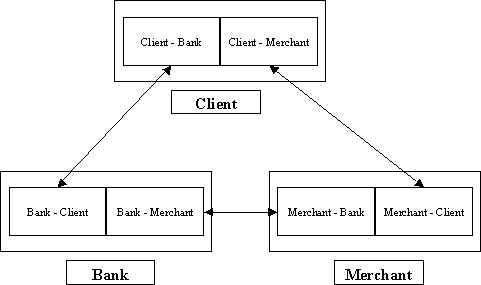
Driver Program interactions with Network Services
Client Specific Elements
A client will support up to two socket connections at one time: one to the bank and one to a merchant.
Bank Specific Elements
The bank is considered to be a network server and as such will run around the clock. It will support an arbitrary number of client and/or merchant socket connections at one time. Each connection will be handled by an individual thread. The assumption is that the bank server is physically secure.
Merchant Specific Elements
The merchant is considered to be a network server and as such will run around the clock. It will support an arbitrary number of client socket connections and it will also support an arbitrary number of connections to the bank. Each connection will be handled by an individual thread.
Comments
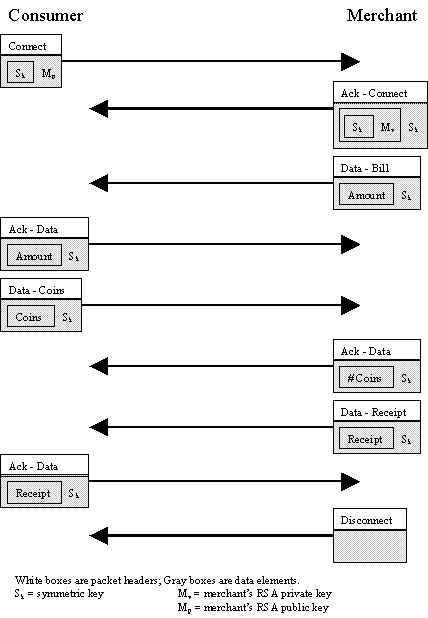
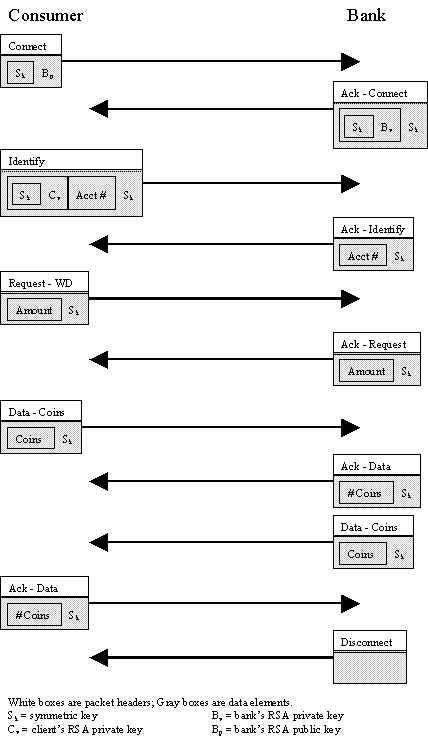
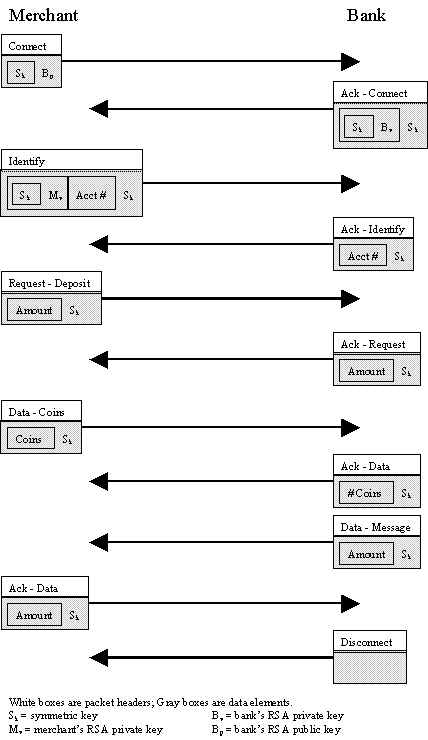
All communications will occur over TCP sockets.
All communications will use the following packet format:
Packet Format
| Header | Type (see Table 1) |
| Subtype (see Table 2) | |
| Length | |
| Header Checksum | |
| Data | Data + Data Checksum |
| Type | Users | Description |
| Connect | Client, Merchant | Establishment of a symmetric key for encryption across the network |
| Identify | Client, Merchant | Identification of the client/merchant and the associated account number |
| Request | Client, Merchant | Request from the client/merchant to the bank |
| Data | Client, Merchant, Bank | Sending data/messages |
| Acknowledge | Client, Merchant, Bank | Acknowledge receipt of packets |
| Error | Client, Merchant, Bank | Indicate that a packet was not successfully received |
| Disconnect | Merchant, Bank | Disconnect |
| Subtype | Users | Description |
| Connect – None | ||
| Identify – None | ||
| Request – Withdrawal | Client | Request for withdrawal from an account |
| Request – Deposit | Client, Merchant | Request for deposit to an account |
| Request - Change | Client | Request for change |
| Data – Coins | Client, Merchant, Bank | Coins for withdrawal/deposit |
| Data – Bill | Merchant | Bill for items purchased |
| Data – Receipt | Merchant | Receipt for items purchased |
| Data – Message | Bank | Valid/invalid coins |
| Acknowledge – Connect | Merchant, Bank | Acknowledge symmetric key for encryption |
| Acknowledge – Identify | Bank | Acknowledge identity of client/merchant |
| Acknowledge – Request | Bank | Acknowledge request for withdrawal/deposit |
| Acknowledge – Data | Client, Merchant, Bank | Acknowledge data |
| Error – Connect | Merchant, Bank | Symmetric key for encryption not received |
| Error – Identify | Bank | Identity of client/merchant not valid |
| Error – Request | Bank | Request for withdrawal/deposit not accepted |
| Error – Data | Client, Merchant, Bank | Data not valid |
| Disconnect – None |
Length
Length in bytes of the data section (including data checksum).
Header Checksum
Checksum of the data in the header.
Each side of the communication will be handled by an appropriate message packet processor. The message processor will be specific to each of the three units. The packets that need to be handled by each unit are labeled above in the packet format specification.
The following functions are implemented:
BankProcessMessage( // process message packets received by the bank // and respond with a packet Input: message packet Output: none ) Consumer: ProcessMerchantMessage( // process message packets received from the merchant // and respond with a packet Input: message packet Output: none ) ProcessBankMessage( // process message packets received from the bank // and respond with a packet Input: message packet Output: none ) Merchant: ProcessConsumerMessage( // process message packets received from the consumer // and respond with a packet Input: message packet Output: none ) ProcessBankMessage( // process message packets received from the bank // and respond with a packet Input: message packet Output: none )
We used Wei-Dai's Crypto++ cryptographic library. This can be found at http://www.eskimo.com/~weidai/cryptlib.html. We wrote wrappers for the functionality that we needed, and added functions to implement blinding. The following function definitions are implemented :
DESCrypto (Symmetric) unsigned int Encrypt(const byte *inBlock, byte * outBlock, unsigned int length); inBlock must have size greater than or equal to length outBlock must have size greater than or equal to length + 16 (because 9 to 16 bytes of padding) length is the amount of inBlock that will be encrypted return value is the number of data bytes in outBlock (including padding) unsigned int Decrypt(const byte *inBlock, byte * outBlock, unsigned int length); inBlock must have size greater than or equal to length outBlock must have size greater than or equal to length length is the amount of inBlock that will be decrypted return value is the number of data bytes in outBlock (because padding is removed) DESCrypto constructor takes a char * (null terminated string) so be careful when generating random strings for symmetric encryption.. RSAPrivateCrypto and RSAPublicCrypto (Asymmetric) void Encrypt(const byte *inBlock, byte * outBlock, unsigned int length); inBlock must have size greater than or equal to length outBlock must have size greater than or equal to 64 (because inBlock padded to 64 bytes) length is the amount of inBlock that will be encrypted (must be less than or equal to 53) unsigned int Decrypt(const byte *inBlock, byte * outBlock); inBlock must have size equal to 64 (because 64 bytes always decrypted) outBlock must have size greater than or equal to 53 (because padding is removed) return value is the number of data bytes in outBlock (because padding is removed) void Sign(const byte *inBlock, byte * outBlock, unsigned int length); inBlock must have size greater than or equal to length outBlock must have size greater than or equal to 64 (because inBlock padded to 64 bytes) length is the amount of inBlock that will be encrypted (must be less than or equal to 53) unsigned int Recover(const byte *inBlock, byte * outBlock); inBlock must have size equal to 64 (because 64 bytes always decrypted) outBlock must have size greater than or equal to 53 (because padding is removed) return value is the number of data bytes in outBlock (because padding is removed) void Blind(Integer& blindingFactor, const Integer plaintext, Integer& blindtext); blindingFactor is initialized inside plaintext is the text to blind blindtext is the blinded text void SignBlind(const Integer plaintext, Integer &signtext); plaintext is the text to sign signtext is the signed text bool Unblind(Integer blindingFactor, const Integer plaintext, Integer& blindtext); blindingFactor is used to unblind text plaintext is the original text to compare to blindtext is the blinded signed text that will be unblinded return value: true if blindtext equals plaintext signed, false otherwise
Cryptographic services only communicate with the driver program. The user's RSA key pair and the bank's public keys are stored locally. The user's private key is accessed via a password generated by the user (not implemented 4/27). The bank acts as a certificate authority.
The cryptography service provides a core virtual class, with generic methods for generating prime numbers and random numbers, as well as a method for generating a checksum for a byte of data and hashing a block of data. Within this core class, we provide a separate class for each encryption algorithm (symmetric and asymmetric). Each of these classes includes methods for encryption, decryption, and key generation - a single key for the symmetric algorithm, and a key pair for the asymmetric algorithm. In addition, the asymmetric class also contains signature methods for signing and verification, as well as blinding methods.
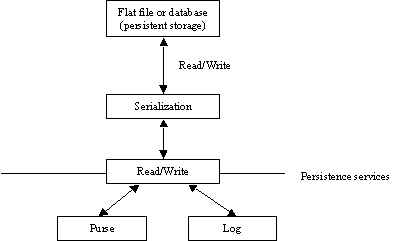
Methods:
Abstractions:
Coin – Data format for v-óa$h coins
Bytes |
|
Serial Number |
4 |
Checksum |
2 |
Purse – Format for storing client coin information during execution
| Total Amount | |
| Denom0 | |
| ... | List of Coins |
| Denom9 | |
Methods:
Log – Format for storing log
Entries as defined in specs |
… |
… |
… |
… |
… |
Methods: