Domain Type Enforcement
Lecturer: Professor Fred B. Schneider
Lecture notes by
Lynette I. Millett
Consider a new kind of matrix. It
looks like the access control matrix but, this is only a superficial
resemblance. The rows in this matrix correspond to domains
and the columns to types. Each entry contains a set of access
rights. An entry [s,t] is the maximum permissions that domain s has
with respect to an object of type t. In contrast to an access control
matrix, this type enforcement matrix does not have commands associated
with it. It cannot be manipulated by owners of objects; instead, it is
controlled by system administrators (MAC as opposed to DAC).
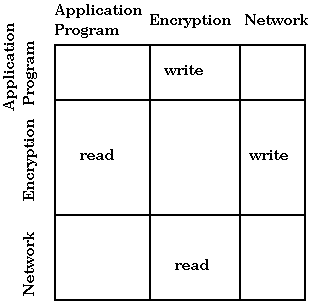
Consider the following example: a program sends data to an
encryption routine that then sends encrypted data to the network. We
would like an application program to be able to write to the
encryption routine. The encryption routine should be able to read from
the application program and write encrypted data to the network, and
the network should be able to read from the encryption routine. The
matrix is as follows:
 This matrix provides stronger constraints than simply making the
encryption routine a trusted subject. A trusted subject can do what it
wants, but here we make the encryption program's access rights more
restrictive. Thus, if we still wish to do an analysis of the
encryption program (e.g. to make sure any data that it writes is
encrypted), we don't know need to worry about it writing anywhere
other than to the network, so the scope of the analysis is narrowed
(and therefore the analysis is easier.)
This matrix provides stronger constraints than simply making the
encryption routine a trusted subject. A trusted subject can do what it
wants, but here we make the encryption program's access rights more
restrictive. Thus, if we still wish to do an analysis of the
encryption program (e.g. to make sure any data that it writes is
encrypted), we don't know need to worry about it writing anywhere
other than to the network, so the scope of the analysis is narrowed
(and therefore the analysis is easier.)

