My research spans operating systems,
networking and distributed systems.
My current projects involve a novel secure operating system and system infrastructure
for high-performance cloud computing applications.
I like building things, especially
systems that have some principled reason for why they should work.
Recent Work |
| HyperDex |
HyperDex is a new NoSQL key-value store. It is fast, consistent, and fault tolerant, with a rich API that includes an efficient search primitive. It is significantly faster than Cassandra, MongoDB and Redis; scales well; and provides a level of consistency and fault tolerance not found in other systems.
|
| OpenReplica |
OpenReplica is a service for replicating objects based on our ConCoord Paxos imlementation for replica coordination. The OpenReplica service enables anyone to quickly and easily replicate objects, to locate replicas through DNS, and to dynamically modify the replica set. It's comparable to Yahoo's ZooKeeper and Google's Chubby, except we run the system as a service, therefore anyone can deploy replicated objects simply by uploading a Python object. OpenReplica achieves performance that is comparable to or better than ZooKeeper for less than 6 replicas.
|
| Nexus |
I am building a new operating system called Nexus. Nexus introduces a new driver architecture, new abstractions and new mechanisms that enable secure, trustworthy applications. The system boots standalone on x86 platforms ideally equipped with TPMs; it can send mail, play movies, run cloud applications and execute Linux programs.
|
| Merlin |
Merlin is a new network management framework that allows administrators to express policies in a high-level, declarative language.
Overall, Merlin simplifies the task of network administration by providing high-level abstractions for specifying network policies and scalable infrastructure for enforcing them.
|
Peer-to-peer Systems |
| Cubit |
Cubit is a peer-to-peer overlay that enables approximate searches in large networks with no centralized components. Given a potentially misspelled keyword, Cubit finds all objects containing that keyword. The project was inspired by the various legal attacks and attempts to take down torrent sites. The key idea behind Cubit is to construct a metric space for keywords, map it onto nodes in a small world, and then to traverse the nodes using a greedy routing algorithm. We have implemented Cubit as an Azureus plugin.
|
| Octant |
Octant is a system for determining the physical location of Internet hosts. Given a host, Octant determines the boundaries of the region in which the node is likely to lie. Behind the scenes, Octant consists of two parts: a comprehensive framework for efficiently representing and combining a system of constraints, and a set of mechanisms for extracting tight constraints on node locations without resulting in
an overconstrained system.
|
| Meridian |
Meridian is a peer-to-peer overlay network for performing location-aware node and path selection in large-scale distributed systems. It is simple to deploy, robust to
churn, and can accurately find the nearest node, pick the most centrally placed node, and find a node that fits latency constraints.
|
| Beehive CoDoNS CobWeb CorONA
|
Beehive is a high-performance distributed hash table. A novel
optimization technique enables Beehive to respond to queries
quickly, tolerate
denial of service attacks, and balance load. Beehive provides
strong performance guarantees even in the presence of queries
drawn from Power Law distributions, previously thought to be
difficult because heuristics-based approaches tried in the past do not
work well with such distributions.
We have used
Beehive to build new, resilient infrastructure services for the
Internet. CoDoNs is a
safety net and a replacement for the Domain Name System that
provides strong security, performance, and fast
dynamic updates for existing Internet names.
CobWeb is an Akamai-like
open-access content distribution network.
CorONA is a high-performance publish-subscribe system for web micronews.
|
| Sqrt(S)
|
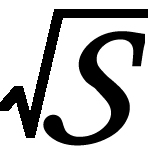 is a practical and efficient failure detector.
It is particularly suitable for systems where a node is tasked with monitoring the liveness status of a
large number of other nodes, such as peer-to-peer systems.
It determines how often to monitor each node such that failure detection latency
is minimal while bandwidth usage remains below a user-specified limit. Unlike
most other work on theoretical failure detectors, it is not only usable in real systems, but also simple and efficient.
is a practical and efficient failure detector.
It is particularly suitable for systems where a node is tasked with monitoring the liveness status of a
large number of other nodes, such as peer-to-peer systems.
It determines how often to monitor each node such that failure detection latency
is minimal while bandwidth usage remains below a user-specified limit. Unlike
most other work on theoretical failure detectors, it is not only usable in real systems, but also simple and efficient.
|
| Credence |
Credence is a reputation system for peer-to-peer networks, designed to
provide an accurate metric for the trustworthiness of labels associated
with shared files. It differs from previous work in that it derives
its trust metric from principled measures that reflect likelihood
of similar behavior between peers, has a completely
distributed architecture with no trusted nodes, and a concrete
implementation. Credence can guard against Sybil attacks and
other malicious behavior from
spammers. The Credence implementation is free, open-source,
and backwards compatible with Gnutella.
|
| CorSSO |
CorSSO is a distibuted authentication service that provides
network identities that span multiple application services, also
known as single sign-on. It enables authentication functionality
to be factored out of application services and delegated to
combinations of authentication servers. It uses threshold
cryptography for efficiency, fault tolerance and resiliance
against attackers.
|
| Karma |
Karma is a virtual currency for use in keeping track of users'
resource contribution and consumption in peer-to-peer systems.
The karma system provides a secure exchange mechanism for a
self-regulating, incentive-compatible, decentralized currency.
|
| Herbivore |
Herbivore is a peer-to-peer, self-organizing, robust system for
anonymous communication. It uses dining cryptographer networks
to provide anonymity guarantees even in the presence of attackers
which can eavesdrop on every packet in the network.
It's a follow-on to the
CliqueNet project.
|
Operating Systems and Virtual Machines |
| Nexus |
I am building a new operating system called Nexus. Nexus introduces a new driver architecture, new abstractions and new mechanisms that enable secure, trustworthy applications. The system boots standalone on x86 platforms ideally equipped with TPMs; it can send mail, play movies, run cloud computing applications and execute Linux programs.
|
| Trickles |
Trickles is a high-performance protocol for stateless, connection-oriented
communication. It comprises a transport protocol to replace TCP and a
new interface to replace sockets that allow all server-side state
to be shipped to clients. This leads to applications that are
more scalable and robust against denial-of-service attacks. And it
enables a new class of services:
since a stateless network stack allows packets to be serviced at
any server replica regardless of past history, Trickles enables
fast transparent failover, fine-grain load balancing and
connection-oriented anycast services to be implemented
transparently inside the network fabric.
|
| Portos |
Portos is an emulation-based system and a set of corresponding
projects that I use to teach introductory-level
operating systems. The projects cover traditional topics, as well as new issues (such as routing and self-organization) raised by mobile, ubiquitous computing. The base emulation framework emulates a virtual processor, with attached
virtual devices, on Windows NT (including 98/ME/XP/etc.) and CE. It runs on x86 and StrongArm processors. It's freely available.
|
| Kimera |
The goal of the Kimera project is to enable networks of computers that
are cheaper, more secure and more manageable than what we have
now. The problem with current state of the art systems, like Java, is that network clients are monolithic, that is, they implement all requisite
system services locally. Consequently, every endpoint needs to
have sufficient resources to support services like verification,
compilation and security management, which require too much memory
and processing power for embedded devices. Further, each endpoint
entails associated software state that is hard to secure and manage.
These problems become particularly acute as the number of clients
increases.
The Kimera project addresses these problems by factoring system
components out of clients into network servers. The clients can thus
be smaller because they do not have to support complex services locally.
Further, the overall network is easier to manage because service
functionality is centralized. The services operate by intercepting
applications as they are fetched by clients; they inspect applications, and where necessary, inject code snippets into them to provide the requisite service
functionality. Digital signatures ensure that only applications that
have been vetted by centralized services execute on the clients.
|
| SPIN
|
The goal of the SPIN project is to enable applications to customize
operating system functionality by downloading application-specific
extensions dynamically into the kernel. The extensions, as well as the
core system, are written in Modula-3, whose type-safety ensures load
and store protection. A namespace management interface restricts the
interfaces that applications can access, and creates multiple
software protection domains within a single privileged address space.
The SPIN execution model enables applications to safely extend the
kernel with thread packages and hierarchical scheduling policies. A
combination of language and system mechanisms provide security and
fault-isolation while mediating access to processors. The SPIN
protection domain interface simultaneously allows isolation and safe
fine-grain sharing within a privileged address space. Extensions
reside in hierarchical namespaces which they can use to share or to
hide code and data at the granularity of interfaces. Use of
hierarchical capabilities simplifies security management. Extensions
that want to safely share code and data can do so without dynamic
protection enforcement overhead. The SPIN web server uses all of these
mechanisms to implement high-performance web service.
|
| MIPSI |
MIPSI is a robust and extensive MIPS instruction set simulator.
It has been used in many classes and research
projects.
|
Ad Hoc Networks |
| MagnetOS |
MagnetOS is an operating system for ad hoc networks. It makes the entire
network appear as a single Java virtual machine. It enables applications
to be constructed easily and to execute efficiently.
|
| Sextant |
Sextant is a general framework for discovering the location of
nodes and events in wireless networks. Sextant enables nodes without
specialized hardware, such as GPS, to efficiently discover their
approximate locations. Further, given a sensor network where each node
can sense events in its immediate vicinity, Sextant pinpoints the
location of events with high fidelity.
|
| SHARP |
SHARP is a hybrid routing protocol that dynamically finds the optimal
mix of proactive route dissemination and reactive route discovery to
achieve application-specific performance goals.
|
| SNS |
SNS is a scalable, high-performance wireless network simulator,
based on ns2. It vastly outperforms standard ns2 in speed and scale through a new technique we developed called staged simulation. It achieves
its improvements in speed and scale by eliminating redundant computations both
within a single and across multiple simulation runs. It has been carefully
validated against ns2 - staging preserves accuracy while speeding up simulations.
|
A Content Propagation Metric for Efficient Content Distribution.
Ryan S. Peterson, Bernard Wong, and Emin Gün Sirer.
In Proceedings of the SIGCOMM Conference, Toronto, Canada, August 2011.
Blindfold: A System to See No Evil in Content Discovery.
Ryan S. Peterson, Bernard Wong, and Emin Gün Sirer.
In Proceedings of the International Workshop on Peer-to-Peer Systems, San Jose, California, April 2010.
AntFarm: Efficient Content Distribution with Managed Swarms.
Ryan Peterson and Emin Gün Sirer.
In Proceedings of the Symposium on Networked System Design and Implementation, Boston, Massachusetts, April 2009.
Going Beyond Tit-for-Tat: Designing Peer-to-Peer Protocols for the Common Good.
Ryan Peterson and Emin Gün Sirer.
In Proceedings of the Workshop on Future Directions in Distributed Computing, Bertinoro, Italy, June 2007.
A Practical Approach to Peer-to-Peer Publish-Subscribe.
Ryan Peterson, Venugopalan Ramasubramanian, and Emin Gün Sirer.
In ;login:, 31(4):42--46, 2006.
Corona: A High Performance Publish-Subscribe System for the World Wide Web.
Venugopalan Ramasubramanian, Ryan Peterson, and Emin Gün Sirer.
In Proceedings of the Symposium on Networked System Design and Implementation, San Jose, California, May 2006.
Heuristics Considered Harmful: Using Mathematical Optimization for Resource Management in Distributed Systems.
Emin Gün Sirer.
In IEEE Intelligent Systems, Special Issue on Self-Management through Self-Organization in Information Systems, 21(2), 2006.
Optimal Resource Utilization in Content Distribution Networks.
Yee Jiun Song, Venugopalan Ramasubramanian, and Emin Gün Sirer.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2005-2004, 2005.
A Measurement Study of RSS, A Publish-Subscribe System for Web Micronews.
Hongzhou Liu, Venugopalan Ramasubramanian, and Emin Gün Sirer.
In Proceedings of the Internet Measurement Conference, Berkeley, California, October 2005.
Perils of Transitive Trust in the Domain Name System.
Venugopalan Ramasubramanian and Emin Gün Sirer.
In Proceedings of the Internet Measurement Conference, Berkeley, California, October 2005.
The Design and Implementation of a Next Generation Name Service for the Internet.
Venugopalan Ramasubramanian and Emin Gün Sirer.
In Proceedings of the SIGCOMM Conference, Portland, Oregon, August 2004.
Beehive: 0(1) Lookup Performance for Power-Law Query Distributions in Peer-to-Peer Overlays.
Venugopalan Ramasubramanian and Emin Gün Sirer.
In Proceedings of the Symposium on Networked System Design and Implementation, San Francisco, California, March 2004.
Proactive Caching for Better than Single-Hop Lookup Performance.
Venugopalan Ramasubramanian and Emin Gün Sirer.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2004-1931, 2004.
Eluding Carnivores: File Sharing with Strong Anonymity.
Emin Gün Sirer, Sharad Goel, Mark Robson, and Dogan Engin.
In Proceedings of the European SIGOPS Workshop, Leuven, Belgium, September 2004.
Herbivore: A Scalable and Efficient Protocol for Anonymous Communication.
Sharad Goel, Mark Robson, Milo Polte, and Emin Gün Sirer.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2003-1890, 2003.
CliqueNet: A Self-Organizing, Scalable, Peer-to-Peer Anonymous Communication Substrate.
Emin Gün Sirer, Milo Polte, and Mark Robson.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2001, 2001.
Comprehensive Synchronization Elimination for Java.
Jonathan Aldrich, Emin Gün Sirer, Craig Chambers, and Susan Eggers.
In Science of Computer Programming, 47(2):91--120, 2003.
Design and Implementation of a Distributed Virtual Machine for Networked Computers.
Emin Gün Sirer, Robert Grimm, Arthur J. Gregory, and Brian N. Bershad.
In Proceedings of the Symposium on Operating Systems Principles, Kiawah Island, South Carolina, December 1999.
Testing Java Virtual Machines.
Emin Gün Sirer and Brian N. Bershad.
In Proceedings of the International Conference on Software Testing And Review, San Jose, California, November 1999.
Using Production Grammars in Software Testing.
Emin Gün Sirer and Brian N. Bershad.
In Proceedings of the Conference on Domain-Specific Languages, Austin, Texas, October 1999.
Eliminating Unnecessary Synchronization from Java Programs.
Jonathan Aldrich, Craig Chambers, Emin Gün Sirer, and Susan Eggers.
In Proceedings of the Static Analyses Symposium, Venice, Italy, September 1999.
A Practical Approach for Improving Startup Latency in Java Applications.
Emin Gün Sirer, Arthur J. Gregory, and Brian N. Bershad.
In Proceedings of the Workshop on Compiler Support for System Software, Atlanta, Georgia, May 1999.
Distributed Virtual Machines: A System Architecture for Network Computing.
Emin Gün Sirer, Robert Grimm, Brian N. Bershad, Arthur J. Gregory, and Sean McDirmid.
In Proceedings of the European SIGOPS Workshop, Sintra, Portugal, September 1998.
Improving the Security, Scalability, Manageability and Performance of System Services for Network Computing.
Emin Gün Sirer, Robert Grimm, Arthur J. Gregory, Nathan R. Anderson, and Brian N. Bershad.
University of Washington, Seattle, Washington, Technical Report UW-CSE-98-09-01, 1998.
Design and Implementation of a Single System Image Operating System for Ad Hoc Networks.
Hongzhou Liu, Tom Roeder, Kevin Walsh, Rimon Barr, and Emin Gün Sirer.
In Proceedings of the International Conference on Mobile Systems, Applications, and Services, Seattle, Washington, June 2005.
On the Need for System-Level Support for Ad hoc and Sensor Networks.
Rimon Barr, John C. Bicket, Daniel S. Dantas, Bowei Du, T.W. Danny Kim, Bing Zhou, and Emin Gün Sirer.
In SIGOPS Operating Systems Review, 36(2):1--5, 2002.
Automatic Code Placement Alternatives for Ad Hoc and Sensor Networks.
Emin Gün Sirer, Rimon Barr, T.W. Danny Kim, and Ian Yee Yan Fung.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2001-1853, 2001.
Octant: A Comprehensive Framework for the Geolocalization of Internet Hosts.
Bernard Wong, Ivan Stoyanov, and Emin Gün Sirer.
In Proceedings of the Symposium on Networked System Design and Implementation, Cambridge, Massachusetts, April 2007.
Geolocalization on the Internet through Constraint Satisfaction.
Bernard Wong, Ivan Stoyanov, and Emin Gün Sirer.
In Proceedings of the Workshop on Real, Large Distributed Systems, Seattle, Washington, November 2006.
ClosestNode.com: An Open-Access, Scalable, Shared Geocast Service for Distributed Systems.
Bernard Wong and Emin Gün Sirer.
In SIGOPS Operating Systems Review, 40(1), 2006.
Meridian: A Lightweight Network Location Service without Virtual Coordinates.
Bernard Wong, Aleksandrs Slivkins, and Emin Gün Sirer.
In Proceedings of the SIGCOMM Conference, Philadelphia, Pennsylvania, August 2005.
Meridian: A Lightweight Network Location Service without Virtual Coordinates (Extended).
Bernard Wong, Aleksandrs Slivkins, and Emin Gün Sirer.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2005-1982, 2005.
A Lightweight Approach to Network Positioning.
Bernard Wong and Emin Gün Sirer.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2004-1949, 2004.
A Rate-Matching Approach to Dynamic Voltage Scaling.
David Biermann, Emin Gün Sirer, and Rajit Manohar.
In Proceedings of the Watson Conference on the Interaction between Architecture, Circuits, and Compilers, New York, New York, October 2004.
On Selection of Optimal Transmission Power for Ad hoc Networks.
Yurong Chen, Emin Gün Sirer, and Stephen B. Wicker.
In Proceedings of the Hawaii International International Conference on Systems, Hawaii, January 2003.
Path-Set Selection in Mobile Ad Hoc Networks.
Panagiotis Papadimitratos, Zygmunt Haas, and Emin Gün Sirer.
In Proceedings of the International Symposium on Mobile Ad Hoc Networking and Computing, Lausanne, Switzerland, June 2002.
An Access Control Language for Web Services.
Emin Gün Sirer and Ke Wang.
In Proceedings of the ACM Symposium on Access Control Models and Technologies, Monterey, California, June 2002.
Logical Attestation: An Authorization Architecture for Trustworthy Computing.
Emin Gün Sirer, Willem de Bruijn, Patrick Reynolds, Alan Shieh, Kevin Walsh, Dan Williams, and Fred B. Schneider.
In Proceedings of the Symposium on Operating Systems Principles, Cascais, Portugal, October 2011.
NetQuery: A Knowledge Plane for Reasoning about Network Properties.
Alan Shieh, Emin Gün Sirer, and Fred B. Schneider.
In Proceedings of the SIGCOMM Conference, Toronto, Canada, August 2011.
Nexus Authorization Logic: Design Rationale and Applications.
Fred B. Schneider, Kevin Walsh, and Emin Gün Sirer.
In ACM Transactions on Information and System Security, 14(1), 2011.
Device Driver Safety Through a Reference Validation Mechanism.
Dan Williams, Patrick Reynolds, Kevin Walsh, Emin Gün Sirer, and Fred B. Schneider.
In Proceedings of the Symposium on Operating System Design and Implementation, San Diego, California, December 2008.
Securing BGP Using External Security Monitors.
Patrick Reynolds, Oliver Kennedy, Emin Gün Sirer, and Fred B. Schneider.
Cornell University, Computing and Information Science, Ithaca, New York, Technical Report TR2006-2065, 2006.
Nexus: A New Operating System for Trustworthy Computing.
Alan Shieh, Dan Williams, Emin Gün Sirer, and Fred B. Schneider.
In Proceedings of the Symposium on Operating Systems Principles, Extended Abstract, Brighton, United Kingdom, October 2005.
Optimal Parameter Selection for Efficient Memory Integrity Verification Using Merkle Hash Trees.
Dan Williams and Emin Gün Sirer.
In Proceedings of the International Symposium on Network Computing and Applications, Trusted Network Computing Workshop, Boston, Massachusetts, August 2004.
Strands: An Efficient and Extensible Thread Management Architecture.
Emin Gün Sirer, Przemyslaw Pardyak, and Brian N. Bershad.
University of Washington, Seattle, Washington, Technical Report UW-CSE-97-09-01, 1997.
Low-level Systems Programming with Modula-3.
Marc E. Fiuczynski, Wilson Hsieh, Emin Gün Sirer, Przemyslaw Pardyak, and Brian N. Bershad.
In Threads, Modula-3 Systems Journal, 3(4), 1997.
Safe Dynamic Linking in an Extensible Operating System.
Emin Gün Sirer, Marc Fiuczynski, Przemyslaw Pardyak, and Brian N. Bershad.
In Proceedings of the Workshop on Compiler Support for System Software, Tucson, Arizona, February 1996.
Writing an Operating System Using Modula-3.
Emin Gün Sirer, Stefan Savage, Przemyslaw Pardyak, Greg DeFouw, and Brian N. Bershad.
In Proceedings of the Workshop on Compiler Support for System Software, Tucson, Arizona, February 1996.
Extensibility, Safety and Performance in the SPIN Operating System.
Brian N. Bershad, Stefan Savage, Przemyslaw Pardyak, Emin Gün Sirer, Marc Fiuczynski, David Becker, Craig Chambers, and Susan Eggers.
In Proceedings of the Symposium on Operating Systems Principles, Copper Mountain, Colorado, December 1995.
Protection is a Software Issue.
Brian N. Bershad, Stefan Savage, Przemyslaw Pardyak, David Becker, Marc Fiuczynski, and Emin Gün Sirer.
In Proceedings of the Workshop on Hot Topics in Operating Systems, Orcas Island, Washington, May 1995.
SPIN - An Extensible Microkernel for Application-specific Operating System Services.
Brian N. Bershad, Craig Chambers, Susan Eggers, Chris Maeda, Dylan McNamee, Przemyslaw Pardyak, Stefan Savage, and Emin Gün Sirer.
In SIGOPS Operating Systems Review, 29(1):74--77, 1995.
SPIN - An Extensible Microkernel for Application-specific Operating System Services.
Brian N. Bershad, Craig Chambers, Susan Eggers, Chris Maeda, Dylan McNamee, Przemyslaw Pardyak, Stefan Savage, and Emin Gün Sirer.
In Proceedings of the European SIGOPS Workshop, Dagstuhl, Germany, September 1994.
SPIN - An Extensible Microkernel for Application-specific Operating System Services.
Brian N. Bershad, Craig Chambers, Susan Eggers, Chris Maeda, Dylan McNamee, Przemyslaw Pardyak, Stefan Savage, and Emin Gün Sirer.
University of Washington, Seattle, Washington, Technical Report UW-CSE-94-03-03, 1994.
