Firewall/NAT box classification notes
1 Introduction
This document is a start at what aspects of a system need to be classified in order to know how two peers over the internet may (or may not) be able to directly communicate.
2 System-local classification
This is just a start. Saikat will fill this out.
· LINUX or Windows (or, more to the point, can it do symmetric TCP or not?)
- Can the system manipulate raw socket?
- Does system have TCP-over-UDP?
3 Firewall/NAT box classification
This section lists a number of things a client may need to know about its FW/NAT.
- Is there a NAT box? (Similar to what STUN figures out.)
- Is the NAT box full cone, port restricted, or symmetric? For both TCP and UDP (do any NAT boxes treat TCP and UDP differently…i.e. are one type for TCP and another for UDP)?
- Broad general question is whether there is some way to “fingerprint” a FW/NAT box. This way we can associate behavior with certain kinds of NAT boxes. For instance, linksys boxes are configured via HTTP to a certain IP address. Our test client could talk to that address and see if a linksys responds. A similar thing may be true for other NAT boxes.
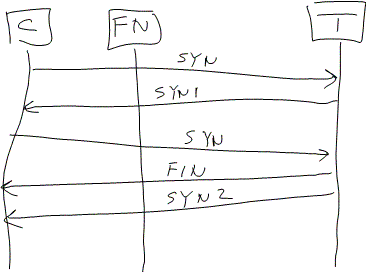
- How does NAT deal with TCP FIN? I.e. does it “close the hole” (that is, remove the NAT mapping) when it receives a FIN for a connection? To test, we can do what is shown in Figure 1. Here, C is client, FN is FW/NAT, and T is our test platform. If SYN2 gets through, we know that the FN keeps the hole open. If not, we know it closes it. (Not shown here is that the client would report to the test platform the results of the test, etc.)
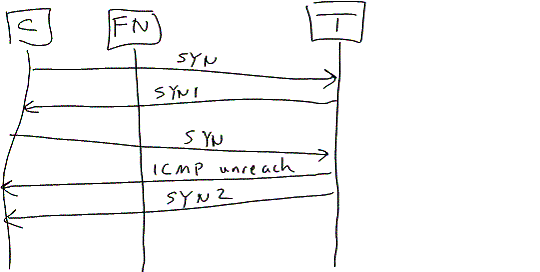
5. How does the NAT box deal with ICMP unreachables? This is similar to the FIN issue, and can be tested the same way, except using ICMP instead of FIN (see Figure 2).
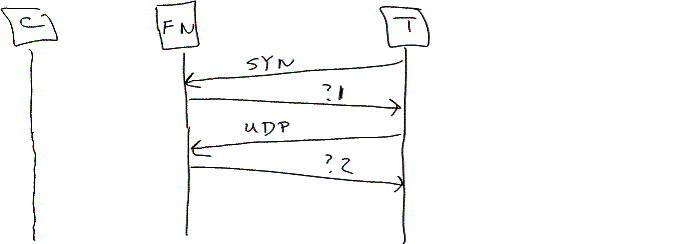
6. What do FW/NAT boxes return when the receive packets with no associated mapping? For instance, do they return RST or ICMP unreachable (for TCP), ICMP unreachable (for UDP), or nothing? Figure 3 shows the test platform sending a SYN or a UDP packet and monitoring what is returned.
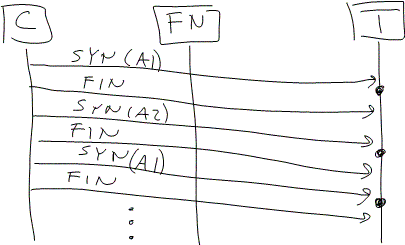
7. If the NAT box is symmetric, can we predict what port it will assign? One way to do that would be to establish lots of connections from the client to the test platform, and monitor what ports are used. (In Figure 4, A1 and A2 refer to addresses of the test platform. The test platform monitors the port assigned at the points identified by the dots in its time line. We could do this for UDP as well.
8. Find out if the policies for closing holes is different for TCP and UDP. For instance,