Lecture 7
Lecturer: Professor Fred B. Schneider
Notes by: Vicky Weissman
Lecture Date: 2/17/00
Today’s Topics
- Kerberos
·
Threats
·
Requirements
·
Protocol
·
Practical
Concerns
Threats
Kerberos was designed to provide authentication, despite passive wiretapping and replay attacks.
Requirements
Kerberos needs to be:
· Reliable
· Transparent
· Scalable – both in terms of the number of supported hosts and in the system’s ability to interact with outside hosts.
In practice, Kerberos's scalability is limited to university-sized communities.
Protocol
Basic Setup:· Kerberos is a key distribution center (KDC); it generates and distributes keys as needed for authentication.
· Kerberos shares a secret key, called a master key, with each host in the network.
· Kerberos maintains a database of these master keys. The database is encrypted using KDC's private key, K KDC.
The 3 main phases of the protocol are given below:
Phase 1: User A gets the credentials that are needed to request access to a service.

Phase 2: User A gets credentials for access to a specific service B.
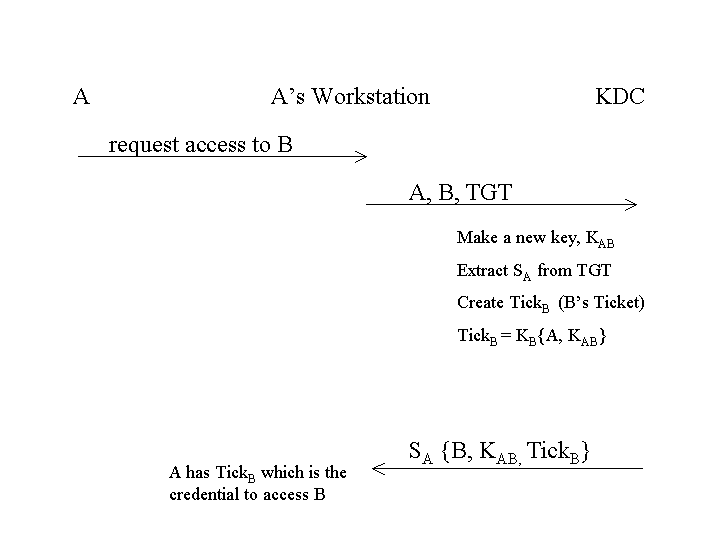
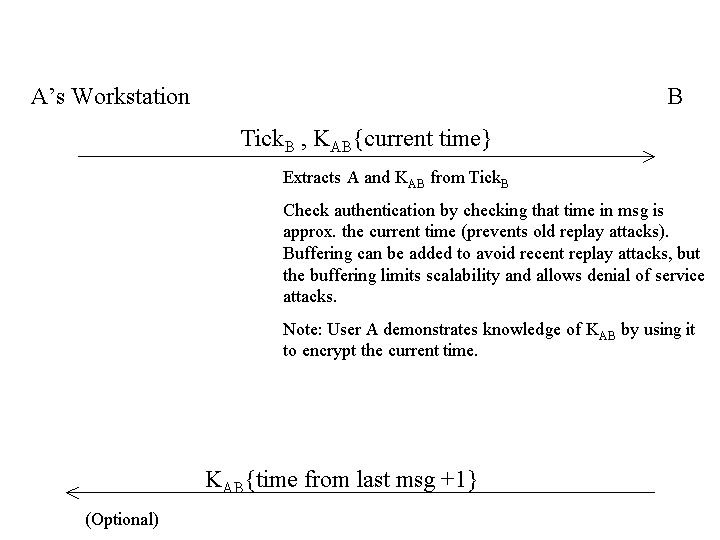
Phase 3: A presents credentials to B
Practical Concerns
· All hosts have to trust KDC
· KDC is a centralized point
o bad for reliability
o bad for performance
Replication can improve reliability and performance. Specifically, we can have a master KDC with a read/write copy of the key database and n replicas that have read-only copies of the database. The databases could have encrypted timestamps to avoid replay attacks and could have encrypted checksums to avoid splicing attacks (split DB and add a new record). A KDC hierarchy can be created to fit the size of the user community.