Lecture 6
Lecturer: Professor Fred B. Schneider
Notes by: Vicky Weissman
Lecture Date: 2/1/00
Today’s Topics
- Definitions:
(diffusion, perfect secrecy, computationally secure, and unconditionally
secure)
- Perfect Substitution
Cipher
- Secret Key Cryptography
diffusion: localized information in the plaintext is spread throughout the corresponding cipher text. (Ex: 2 plaintext messages that differ by a single letter are encrypted to produce 2 cipher texts that are different throughout the text.)
perfect secrecy: the probability that a given message is encoded in the cipher text is unaltered by having the cipher text.
computationally secure: cryptosystem can be broken, if enough processing power is used
unconditionally secure: the ability to break the cryptosystem does not depend on the amount of available processing power
Perfect Substitution Cipher
· algorithm: pick a sequence of random bits, 1 for each bit in the plaintext message. The cipher text is the XOR of the plaintext with the random bits.
· the key is the randomly chosen bits
· cipher provides perfect secrecy
· problems: how are the random sequence of bits generated? how does the receiver know the key?
· first practical implementation by Gilbert Vernam who used 1-time pads to get the key and to facilitate communicating the key
Secret Key Cryptography
Notation:
k{m} = E(k, m) = apply encryption function E, to message m, using key k
D(k, m) = apply decryption function D, to message m, using key k
D(k, E(k, m)) = m, but, in general, K{D(k, m)} ¹ m
authentication maintain secrecy of stored data maintain secrecy despite passive wiretappers Authentication Protocols: Assume that Alice (A) and Bob (B) share a key (KAB) that only they know. Protocol 1: A proves identity by sending KAB to B.
Problems: passive wiretapper can get the key. B gets the key before proving his identity. Features of Protocol 2: ·
random number generation deters replay attacks ·
identity proof does not reveal the key (strong
authentication) ·
identity proof does not convince a 3rd party
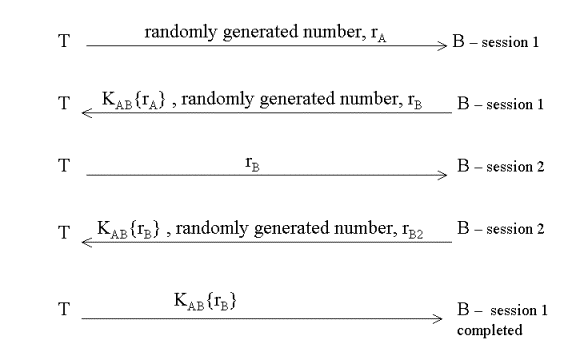
(non-repudiation is not provided) Protocol 3 ( a failed optimization of protocol 2) Attack against Protocol 3: Trudy (T) can convince Bob that she is Alice, by
initiating 2 sessions as follows: Patches for Protocol 3: ·
use 2 keys. Ex:
A sends using one key, B sends using a
different key ·
create asymmetry.
Ex: require the challenge from the initiator to be different from the
challenge from the responder ·
do minimal work until the identity of the other party
is proven