Watermarking JPEG Images
Nikolay Mateev and Lidong Zhou,
Department of Computer Science,
Cornell University, Ithaca, NY 14853
December 8, 1996
1 Introduction
Digital images and video have many advantages over the ordinary form --
they are easy and inexpensive to duplicate, and less expensive to distribute.
On the other hand, that ease of making precise copies of digital media
increases the difficulty of enforcing copyright. As digital images and
video become more popular, there is a pressing need for a scheme to protect
ownership.
We can achieve that by adding a digital label (watermark) to the electronic
media. That label must uniquely identify the copyright owner, and should
also allow distribution of the particular copy to be tracked. In order
to be effective, a watermark must have the following properties:
-
Perceptual invisibility: watermarks should not degrade the quality of the
picture being protected;
-
Robustness: it should be difficult (if not impossible) to remove watermarks
without significantly reducing the quality of the image. In particular,
we would want to be able to retrieve the watermark after the following
manipulations:
-
common signal processing operations such as adding noise, change of brightness,
change of contrast, and requantization;
-
common geometric distortions such as translation, scaling, rotation, and
cropping;
-
collusion by multiple users who possess different watermarked copies of
the data.
In addition, we want the process of adding the watermark to be efficient,
so that it could be used in on-line applications as Video On Demand.
As JPEG and MPEG become compression standards for images and video respectively,
it is meaningful to devise a watermarking method solely for JPEG and MPEG
compressed data. Such a method can take advantage of the specific properties
of image or video compression.
There have been several digital watermarking methods proposed. All of
them work on uncompressed images, which makes them not particularly suited
to our goals. R.G. van Schyndel et al. [vSTO94] proposed a method that
inserts the watermark in the "insignificant" bits. Bits are considered
insignificant if changes in them are not noticeable. That approach does
not work in our case, because JPEG compression throws away those bits and
thus destroys the watermark. Koch, Rindfrey and Zhao [KRZ94] proposed breaking
the picture into 8x8 blocks, performing a Discrete Cosine Transform (DCT)
on each block, and then encoding a 0 or 1 by modifying the relative strengths
of a triple of coefficients in some blocks. Although this method works
in the frequency domain, same as ours, its goal is to mark non-compressed
images and is not very robust to compression. It works for JPEG compression
quality factor of 50% or more, while our method performs well for quality
factor as low as 10%. Cox, Kilian, Leighton and Shamoon [CKLS95] proposed
a spread spectrum method -- they perform DCT on the whole image, transforming
it into the frequency domain, and then embed the watermark in the largest
(visually most significant) coefficients. The watermark is robust and particularly
good against collusion, but their watermarking procedure is very slow,
thus unusable for on-line applications.
We propose a method for watermarking JPEG images during the compression
process. We are taking advantage of the round-off errors during the quantization
step of JPEG compression to store the watermark. The algorithm is very
efficient and the robustness to signal processing and geometric distortions
is comparable to that of the spread spectrum method.
The rest of the paper is organized as follows. In Section 2, we describe
the JPEG compression algorithm and introduce associated terminology. In
Section 3 we show how the round-off errors during the quantization step
can be used to store information. The steps of our watermarking procedure
are given in Section 3.1. In Section 3.2 we explain how to extract the
watermark from an image. Experimental methodology and results are presented
in Section 4. Finally, conclusions and possible extensions are in Section
5.
2 Brief Review of JPEG
JPEG stands for "Joint Photographic Expert Group". It is now a widely accepted
standard for image compression. For our purpose, we will only outline the
steps for the popular baseline lossy compression. For a detailed treatment
of JPEG, please refer to [Wal91].
-
DCT on each 8x8 block: Given an image, we first divide
it into 8x8 blocks and for each block, we perform a discrete cosine transformation
(DCT). The result of DCT is the set of 64 DCT coefficients. The coefficient
with zero frequency is called "DC coefficient" and the remaining 63 coefficients
are called "AC coefficients". DC coefficient indicates the average value
of the image sample block. For greyscale pictures, it is related to the
overall brightness of the image.
-
Quantization: In the quantization step, each of the
64 DCT coefficients is quantized using a 64-element Quantization Table.
In our implementation, an additional parameter: quantization factor (or
simply called q factor) can be specified to further control the granularity
of the quantization. The default value is 8. The quantization can be represented
in the following formula:
Fq(u,v) = round ( (F(u,v)/ Q(u,v)) * (8/q_factor))
Where F(u,v) is the DCT coefficients before quantization, Q(u,v) is
the quantization table entry, q_factor is the quantization factor and Fq(u,v)
is the quantized coefficient.
-
Zigzag scan, RLE, and Entropy Coding: The quantized
coefficients are reorganized in the special zigzag order and the AC coefficients
are coded by Run Length Encode method (RLE). Finally we use some traditional
lossless entropy coding. Usually, the Huffman coding is exploited.
To simply our presentation and implementation of the watermark scheme,
we ignore all the steps after quantization and denote that format of the
image as semi-compressed data. It is almost trivial to extend the scheme
and make it work directly on the format after RLE. For the final JPEG format,
we only need to do Huffman encoding after placing the watermark, which
is relatively efficient.
3 Watermarking and Detection Algorithms
In JPEG compression, the quantization step consists of scaling and rounding.
Before the rounding step, we might get a scaled value that is close to
*.5. For example, if the DCT coefficient is 22 and the corresponding quantization
table entry is 4, then we get the scaled value 5.5. If we apply the ordinary
rounding, we would get 6, but actually it does not affect the quality too
much whether we round it down to 5 or up to 6. Our approach is to embed
the watermark in these values.
We have to define "close to *.5" precisely before going into details
of the algorithms. That involves a tradeoff between robustness and quality.
Suppose [*.5-a, *.5+a] is
the region considered to be close to *.5, the bigger a
we select, the more values we might use to plant the watermark, the lower
quality the watermarked picture might be. The user can select the appropriate
a
according to the specific requirements of the application. We also decide
not to use DC coefficients so that the watermark is robust to the changes
of the overall brightness.
For the convenience of further discussion, we first give some definitions:
-
Watermark Position File: This is the file that has all the information
about where to plant watermark in the corresponding semi-compressed image
data.
-
Watermark Base Image File: This file stores the watermarked semi-compressed
image data with "0" embedded in each position. It serves as the basis because
"1"s can be embedded by adding 1 to the value in the corresponding position.
3.1 Watermarking Algorithm:
The watermarking algorithm can be divided into two steps: preprocessing
phase and watermarking phase.
-
Preprocessing Phase: Preprocessing takes the original
picture and the parameter a as the inputs, transform
the original image into its semi-compressed format. During the quantization
step, the positions where the watermark information can hide can be identified
according to the given a, and then stored into the position file. We embed
0 in these positions and output as the watermark base image.
-
Watermarking Phase: In this phase, the position file,
base image file (produced by preprocessing) and a specific bit pattern
are provided as the inputs, and we are going to output the semi-compressed
watermarked image data with the given pattern embedded. The major steps
are as follows:
-
Add error-correcting code to the given bit pattern and get the coded watermark
(see [MWS77] for details on error-correcting codes)
-
Embed the coded watermark into the base file with the positions provided
by the position file
-
Repeat the coded watermark until all the spaces are used up
-
Perform the remaining JPEG compression steps to the semi-compressed watermarked
image
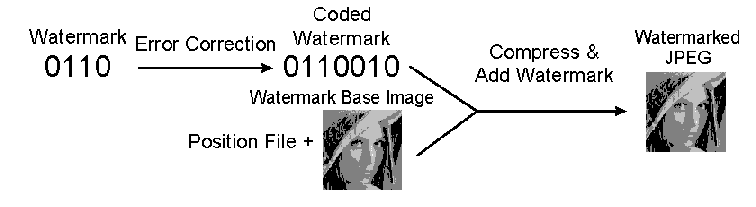
Fig.1: Watermarking Algorithm
To illustrate the procedure, we can go through a simple example shown in
Fig.1. Suppose we want to put watermark 0110; by applying error correction
coding algorithm, we might get coded watermark like 0110010, what we really
put in the picture is the repeated coded watermark: 0110010 0110010 0110010
..., the position information is provided by the position file.
3.2 Watermark Detection Algorithm:
The watermark detection algorithm is illustrated in Fig.2, and we explain
the details below. The input to the algorithm is the watermarked JPEG (possibly
modified or distorted), corresponding original image with its position
file and base file (these two files are not necessary stored, they can
be recomputed) and the output will be the detected watermark in the given
image and the raw statistics that could be used to show how reliable the
result is. There are five major steps:
-
Affine Correction: As the picture might be geometrically distorted, we
first try to adjust it back using some affine transformation. This problem
has been studied in machine vision and methods like optical flow can be
applied to get the coefficients for the transformation. Currently, we implemented
a subset of the algorithm and employ a brute force way to find the best
match.
-
Get the raw repeated coded watermark from the adjusted watermarked image
according to the information provided by position file and base image file.
-
Standardization: as we might get some values that are not 0 or 1, we perform
a standardization step to convert them to binary bits. The conversion is
simply as follows: if b <= 0 then b=0 else b=1.
-
Recover coded watermark: from the standardized repeated coded watermark,
we can try to recover the coded watermark by taking the bit-wise majority.
The information on which the majority decisions are based are stored in
the statistics file.
-
Apply error correction decoding and reveal the watermark.

Fig. 2: Watermark Detection Algorithm
4 Experiments and Evaluations
4.1 Experiments on Quality and a:
As mentioned before, there is a tradeoff between robustness and quality
in selecting a to define the meaning of "close to
*.5", we conducted experiments and the results are summarized in Table
1 below. The results show that we can have a lot of spaces for watermark
without degrading the quality significantly.
|
Size
|
a=0
|
a=0.01
|
a=0.02
|
a=0.05
|
a=0.1
|
|
SNR
|
# of positions
|
SNR
|
# of positions
|
SNR
|
# of positions
|
SNR
|
# of positions
|
SNR
|
|
F-18
|
640x480
|
29.928
|
1794
|
29.927
|
1913
|
29.905
|
5494
|
29.822
|
9433
|
29.476
|
|
flowers
|
640x480
|
23.959
|
4137
|
23.956
|
4710
|
23.950
|
10292
|
23.895
|
25615
|
23.562
|
|
lena
|
120x120
|
24.268
|
136
|
24.262
|
159
|
24.258
|
363
|
24.205
|
771
|
23.961
|
Table 1: The experiments were performed on three images:
F-18.pgm, flowers.pgm and lena.pgm. We use SNR (sound-noise-ratio)
as an indication of the quality. The SNR's listed are for the worst
case, i.e. we round all the values to the direction that causes more loss.
The SNR of an ordinary watermarked picture will be no worse than that.
#
of positions indicates the number of positions we can embed the watermark,
one bit per position. The column with a=0
shows
the SNR's of non-watermarked JPEG images.
4.2 Experiments on Robustness
We devoted a lot of energy into the experiments to test the robustness
of this watermark scheme. In the following experiments, we use a=0.05.
We put 10011100110110110011100101001110 as the watermark into the picture
flowers
and the resulting watermarked picture (click hereto
view the picture) is almost of the same quality as the JPEG picture, its
SNR is 23.905. In all the tables below, columns SNR and Visual
are
used to indicate the quality of the pictures, SNR shows the Sound-to-Noise
Ratio with respect to the original picture, Visual
is the visual
quality of the picture with four levels, A: Excellent, B: OK, C: Bad, and
D: Very Bad. (You can click on this column to view the pictures and judge
the quality for yourself.) The Stat column shows the percentage
of the watermark bits that have been destroyed, the Affine
column
indicates whether any affine adjustment has been performed. Finally Pass/Fail
tells if the watermark is recovered or not.
The first group of attacks is adding random noise (plus 1 or minus 1)
to the DCT coefficients, trying to remove the watermark bits that are hidden
in these coefficients. The results are organized in Table 2 below. Our
detection algorithm fails for the last case, but the quality of that picture
is really low.
|
Parameter
|
SNR
|
Visual
|
Stat
|
Affine
|
Pass/Fail
|
|
10
|
19.700
|
B
|
10.15%
|
No
|
Pass
|
|
20
|
17.483
|
C
|
16.94%
|
No
|
Pass
|
|
30
|
15.967
|
C
|
22.24%
|
No
|
Pass
|
|
45
|
14.344
|
D
|
29.15%
|
No
|
Pass
|
|
60
|
13.190
|
D
|
32.71%
|
No
|
Fail
|
Table 2: Random Noise: Parameter is the number
of AC coefficients per block (63 in total) that have been changed by random
noise.
The second group of attacks is requantization with different q
factor (the default one is q=8). Table 3 shows the
results.
|
Q Factor
|
SNR
|
Visual
|
Stat
|
Affine
|
Pass/Fail
|
|
9
|
23.259
|
A
|
1.43%
|
No
|
Pass
|
|
16
|
18.807
|
B
|
12.56%
|
No
|
Pass
|
|
32
|
19.952
|
C
|
43.84%
|
No
|
Pass
|
Table 3: Requantization
We use xv to perform various transformations, the results are shown
in Table 4:
|
Attack
|
Parameter
|
SNR
|
Visual
|
Stat
|
Affine
|
Pass/Fail
|
|
Scale
|
10% smaller
|
16.139
|
A
|
12.46%
|
Yes
|
Pass
|
|
Scale
|
20% smaller
|
15.334
|
A
|
19.38%
|
Yes
|
Pass
|
|
Scale
|
50% smaller
|
12.318
|
C
|
43.44%
|
Yes
|
Pass
|
|
Scale
|
10% bigger
|
16.139
|
A
|
12.46%
|
Yes
|
Pass
|
|
Scale
|
20% bigger
|
15.934
|
A
|
15.30%
|
Yes
|
Pass
|
|
Rotate
|
-15 degrees
|
7.89
|
C
|
16.95%
|
Yes
|
Pass
|
|
Rotate
|
-30 degrees
|
6.453
|
D
|
24.56%
|
Yes
|
Pass
|
|
Blur
|
3
|
21.102
|
B
|
35.09%
|
No
|
Pass
|
|
Blur
|
7
|
18.282
|
D
|
48.65%
|
No
|
Fail
|
|
Blur + Sharpen
|
3 for blurring
|
20.110
|
A
|
21.11%
|
No
|
Pass
|
|
Smooth
|
-
|
18.046
|
A
|
33.23%
|
No
|
Pass
|
|
JPEG compression
|
10% quality
|
13.710
|
C
|
41.13%
|
No
|
Pass
|
|
JPEG compression
|
5% quality
|
13.297
|
D
|
47.35%
|
No
|
Fail
|
|
Gamma correction
|
2
|
8.191
|
B
|
25.01%
|
No
|
Pass
|
|
Gamma correction
|
3
|
5.359
|
C
|
29.57%
|
No
|
Pass
|
|
Gamma correction
|
4
|
3.977
|
D
|
32.67%
|
No
|
Pass
|
|
Equalize histogram
|
-
|
9.451
|
C
|
30.60%
|
No
|
Pass
|
|
Dim
|
multiple times
|
4.411
|
B
|
26.78%
|
No
|
Pass
|
|
Dull
|
multiple times
|
12.017
|
B
|
28.60%
|
No
|
Pass
|
|
Sharpen
|
multiple times
|
9.860
|
B
|
26.22%
|
No
|
Pass
|
|
Black/White
|
-
|
4.315
|
D
|
41.40%
|
No
|
Pass
|
Table 4. Transformations by xv: The parameters
in this table have the same meanings as those in xv.
These experimental results clearly show that our watermarking scheme is
very robust to almost all of these attacks. Although there are several
failures, the quality of these pictures is so low that we do not really
care too much about this kind of illegal copies. We also ran the same tests
on several other pictures and similar results showed up. From the statistics,
we found out that the errors are very well distributed, thus taking bit-wise
majority of the repeated data really helps in recovering the watermark.
5 Conclusion and Future Work
We have developed a method for watermarking JPEG images that takes advantage
of the round-off errors during the quantization step of JPEG compression.
The quality of the watermarked images is as high as that of the ordinary
JPEG compressed images. The watermark is very robust to signal processing
(changes of brightness and contrast, gamma correction, further compression)
and geometric distortions (scaling, rotation). Moreover, embedding the
watermark is very efficient as it can be performed in the compressed domain,
just before entropy coding. Thus the method can be used in on-line applications
like Video On Demand.
The method described here can easily be extended to MPEG compressed
movies. The idea of hiding information in round-off errors can be used
with any compression method that involves quantization, including some
audio compression schemes. It would make the method even more powerful
if we can find better ways to deal with collusion of multiple users (currently
we can only recover the common part of the watermark, like the copyright
owner) and modify the JPEG decoders to reject pictures with invalid watermarks
would .
6 References:
[CKLS95] I.J. Cox, J. Kiliant, T. Leighton, and T. Shamoon, "Secure spread
spectrum watermarking for multimedia", NEC Research Institute, TR
95-10, 1995
[MWS77] F.J. MacWilliams and N.J.A. Sloane, The Theory of Error-Correcting
Codes,Vols. 1 and 2, North-Holland, Amsterdam, 1977
[KRZ94] E. Koch, J. Rindfrey, and J. Zhao, "Copyright protection for
multimedia data", Proc. of the Int. Conf. on Digital Media and Electronic
Publishing, 1994
[vSTO94] R.G. van Schyndel, A.Z. Tirkel, and C.F. Osborne, "A digital
watermark", Int. Conf. on Image Processing, Vol. 2, pp. 86-90. IEEE,
1994
[Wal91] G.K. Wallace, "The JPEG still picture compression standard",
CACM,
Vol. 34, No. 4, pp. 30-44, 1994


