WHY?
Malicious boot firmware is a potentially serious problem for critical information systems. Boot firmware runs in a fully privileged mode on
bare hardware, prior to the operating system and thus prior to most security mechanisms. It is responsible for loading the operating system
and detecting, initializing, and configuring the hardware where necessary. Most security mechanisms that are used today depend on the
integrity of the host operating system, and make extensive use of operating system services. Thus, malicious boot firmware (residing in
the devices such as keyboards, PCI devices etc.), running before the OS itself could cause serious harm by operating various devices and by
simply corrupting the system.
|
|
HOW?
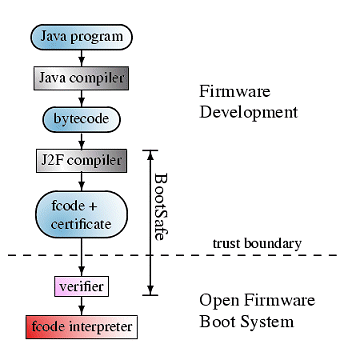
Our BootSafe verifier will be able to detect potentially harmful
firmware with static checks on the compiled code. This process will be very inexpensive, allowing the verification to occur in every boot
cycle. Untrusted firmware will be verified as and allowed to load, since the verification occurs before loading and execution. The
verification process depends on firmware being compiled with a certifying compiler, which produces particularly well-structured and
annotated code. End users only need to trust the verifier in order to be confident in the safety of the compiled code. They do not need to
trust the compiler, nor do they need access to the firmware source code. Thus having the BootSafe verifier on a machine would guarantee
the users that the firmware not harmful.
|
 Welcome to BootSafe Homepage: the Standard of Malicious Code Detection for Open
Firmware
Welcome to BootSafe Homepage: the Standard of Malicious Code Detection for Open
Firmware
 Welcome to BootSafe Homepage: the Standard of Malicious Code Detection for Open
Firmware
Welcome to BootSafe Homepage: the Standard of Malicious Code Detection for Open
Firmware
