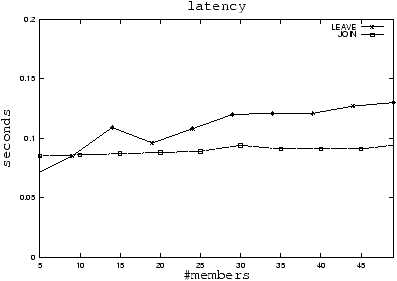
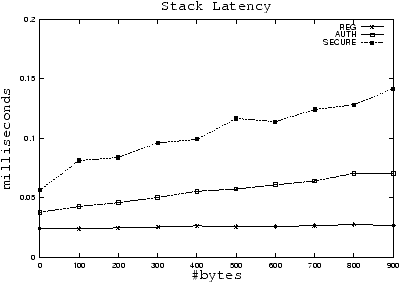
 |
| (1) |
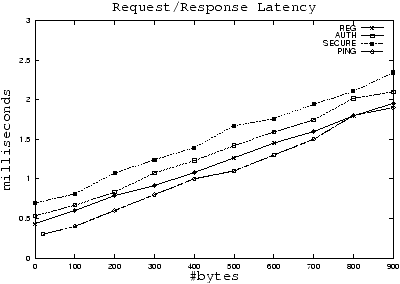 |
| (2) |
 |
| (3) |
Figure 1: A standard stack is denoted REG. An authenticated stack is
denoted AUTH. An authenticated encrypted stack is denoted SECURE.
(1) send-recv latency in the Ensemble stack.
(2) Total Latency for point-to-point send/recv.
(3) Throughput.